App security tips and tricks

I was in two days workshop with Troy Hunt and Here is some notes I took during the workshop to share.
Some thing to remind about Browsers
what you can get from Browsers are:
- Viewing the source gives you the original Html source to view and inspecting element can give you different Html from original source since it might be tweaked after javascript loaded on the page.
- Cookie: It has some properties like affinity - expiry time- Http only,...
- What is Http only? When cookie has this property, it cannot be read by client side
- secure: only be sent over https connection
- samesite: it is for CRSF attack amd not all browsers support it(look at caniuse.com)
- Console: javascript errors- security violation policy,...
Http
When a site is served over Http there are a few problems to discuss.
certificate error
check out badsslto see all possible certification errors.
some sites don't have the pad lock while the site is secure and certification is there. The reason is either images or some other links inside the page are served from insecure Http site which we discuss later again.
favicon:
if the favicon or any image is served from insecure address, browser will load the page without pad lock which is a bad visualized experience. However, if the insecure source is the script , Browser keeps the pad lock but would not load script since it is dangerous.
pasword
somethings to consider for passwords:
It is always the discussion that what should be restricted in terms of strong password?
Some words make the bad words forbidden since if you show the password to the user it is insulting but if you don't recover password you don't need to be worried.
- Minimum lenght for passwords:
Netflix has 4 which is the shortest maybe because users use remote and its hard to type.
Password should have consider the criteria (think of the proper criteria for password) for instance don't let user use the name of site or host.
have i pawnedwebsite look for your email and see how many times your password happened to be in the list of data bridges.
Cross site scripting (XSS)
What is XSS: you can inject a script to alter Dom or change the url or basically any action on the page with javascript inside any textbox like comments in the site .
(check facebook self-xss concept)
reflected XSS
Some browsers has native xss-protection but you need to protect yourself by using encoding. Then no one can put direct script to your site to be executed
html attributes use different encoding than html values and javascript. also URL endoing uses different way of encoding in compare to Html and javascript.
css also uses different way of encoding.
having black list is not a good idea since sometimes you cannot avoid it (e.g names sometimes has ' like Irish names. same as scunthorpe problem which is the city name so it is better to use white-list (regex).
You can use xss-protection mode block and using a service to get and log in a reporting endpoint but it only works in chrome. These days javascript frameworks help us preventing this attack.
top 10 risks owasp
owasp is a community helping with increasing the security level of applications by promoting key factors. Find top 10 application security risk in the pdf
sql injection
It is the first top one from years ago.
notes:
- Only give the permission to your app which is necessary. (prefer readonly if you don't need to be sa)
- look for google dorks
- look for Who can attack our security to see how havij works
- Look at this example to see how broken SQL might be problematic
http://hack-yourself-first.com/Make/1?orderby=@@version*1
Password store
- use the one which don't sell your passwords for 1oG to the browser extensions
- pay for a good one
add blocker
logging data
Ne cautious by logging data. Don't log what you don't really need. some valid sites happened to log plain data last year which is embarrassing.
preferably use external 3th parties like appsight in Azure or New relic instead of your custom one.
Don't just log the things for the sake of debugging code. Consider the security aspect too.
CSRF attack (Cross site request ..)
- You need to use antiforgery for all interactive events even Log out. Once you log in you will have the AuthCookie in your browser for next requests and if we don't have anti forgery token for log off any request any hacker can kick user out by accessing the log out api.
- look at samesite cookie also
Hash cracking
www.onlinehashcrack.com easily realize the hash method you use. if you don't tell people how you store the hashes it means you don't feel secure.
dropbox tell people all the methods they use.
There are even better ways than storing passwords by using Azure active directory or using facebook and other social medias.
practice: Install hashcat and grab a file of hashes (you can even use dic
hashcat64 files
Account enumeration
in registration you would get the error that you are already registered
for some sites like www.AdultFriendFinder.com it is not good to tell a stranger if you have the email to break their privacy. Consider the privacy specially for sites like Addiction website, Health clinic and depression centers, affairs and dating.
in some sites you log in without confirming email (they can register anyone here)
in the other sites they say Email address you entered is already in use so they kind of reveal you are already have account with us.
HTTPS
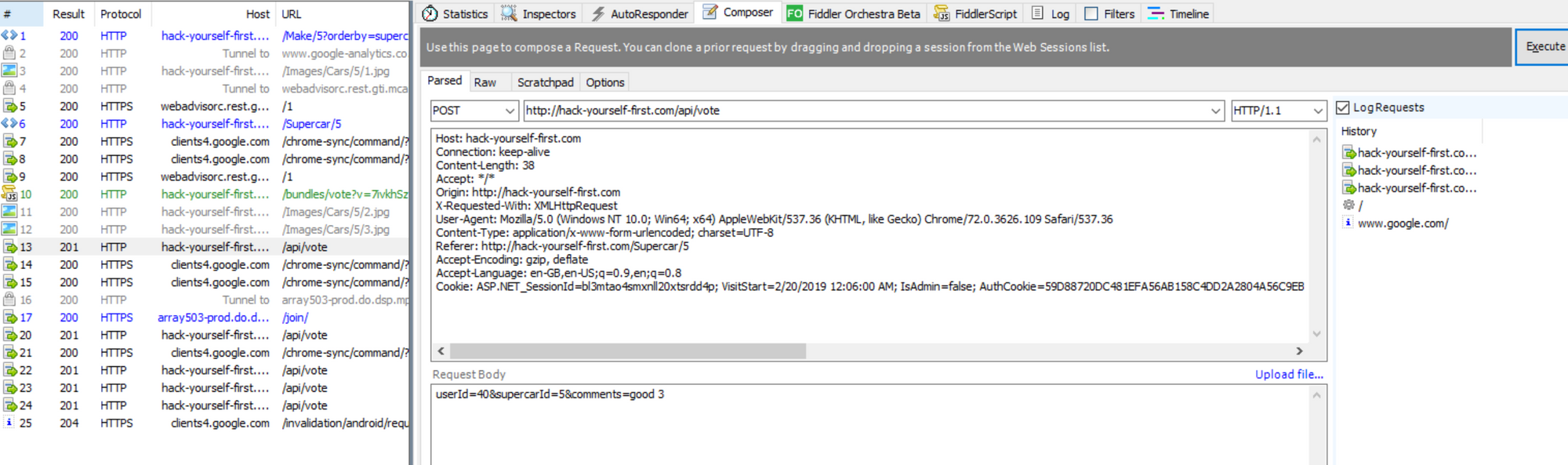
with fiddlerSCript we can change the response and request before and after clients receive them.(use cookbook to learn)
client and server should use same logic otherwise you can change the values of the site by fiddler (e.g prices) and send the submit without back-end checking the logic.
why we need HTTPS?
- confidentiality: you have an encrypted root from client to some servers on the way to serve.
Auth-token: if it is served over https no one can pick the AuthToken fro the browser
Firesheep app used to take the AuthToken from other people's browser over free wifi and impersonate them. - Integrity of response: No one can hijack the response on the way back to client.
- Authenticity: if it is hijacked and redirected on the way then the certificate is not valid anymore means the site is not .
DV (Domain Validation)
site does not mean that the site belongs to a nice ad valid person, even does not mean it is secured.
You can have advanced validation to have the name of the owner just beside the pad lock. But what values does EV really add??
Don't spend money for DV certificate you can get it for free using https://letsencrypt.org/
If you need EV then customers has confidence you are a legitimate organization. But the EV is not proving anything. It is up to the browser to how show the visual indicator they might not show it.Also each browser has its own way for displaying the visual indicator So EV is dying too. More detail
This site gives you the certificate transparency log http://crt.sh. Alternative way is checking Facebook
We discussed that if you have a image in your site served from http, then the pad lock will go away on your site.
To fix that we need to use Content-security-policy:upgrade-insecure-requests
to not consider all children. Even you can go one step further abd set the Content-security-policy-report
You need to do the config somewhere in Server level (IIS), Application level (using NWebsec) or using https://cloudflare.com ,...
if you see https://www.httpvshttps.com/ shows how https can be faster than http by using http2. True it is because Http2 but actually http2 only is available on Https.
Even some compression algorithms are only available over Https like brotli-compression https://scotthelme.co.uk/tag/brotli/
Why you need to serve your static blog on Https? https://www.troyhunt.com/heres-why-your-static-website-needs-https/
the second time the browser will use Strict-transport-security header in response to serve the site for a year over secure connection.
if you add preload in your Strict-transport-security hearder and add it to https://hstspreload.org/ then even the first time someone loads it, it will look at and make sure your site is in the list and serve your site from a secure connection even the first time. So no one can hijack the connection while it is redirecting from Http to Https.
content security policy
You want to run something in someone's site through console but with content security policy you will stop it. in the config you just need to tell the whitelist and declare the websites that can be injecting from so no one can inject and run script from your console.
If you dont do that someone can iframe your web and you get XSF attack (x frame origin attack)
Use soe CDN like https://cloudflare.com
You can put the content policy inside meta or header.
You can also have nonce and hash and all the script in your site get this hash in the script tag and will be whitelisted.
https://www.troyhunt.com/locking-down-your-website-scripts-with-csp-hashes-nonces-and-report-uri/
However if you use policy make sure you use report as well to see what attacks you had. you can also use http://report-uri.com
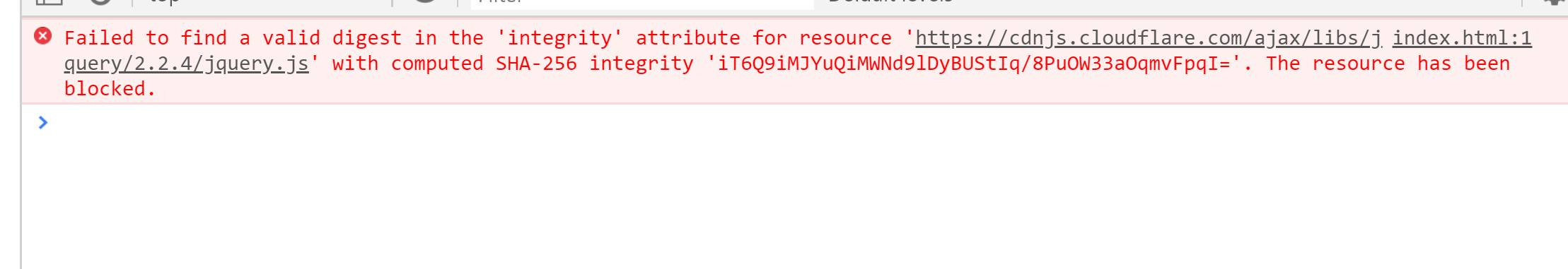
SRI attack
When you download the files from cdn download it with the SRI (integrity)
you can have a content-security-policy to force SIR (require-sri-for script style)
but each time you update the library or bundle , it generated a new hash (might overkill)
if you break the hash code which you downloaded from the CDN it will be broken.
Or we can generate a hash code aginst the script we are using and add it to the script tag in your html.
nonce should potentially be used for static script blocks since any character change in the script will stop the page from loading.
Brute attack
the story is about exposing one of the Quantas boards pass which helps a hacker to impersonate the person and log in to the system.
So CAPTCHA is a solution but it makes trouble for people with disability and ...
Blocking the resource or IP of hackers,...
you need a strategy to tackle these unsuccessful logins.
https://krebsonsecurity.com/
if you try different websites you will see there is not a consistent pattern. every site does different things. lock your ip, lock your Id, captcha,....
netsparker
automation tool to analyse your site.
You have https://www.troyhunt.com/tag/netsparker/ or https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project or
https://portswigger.net/burp or
it figure out certificate transparency or sql injection or ...
report security issue
you need to have a page named .well-known/security.txt
which basically tells you if you found any security problem how contact us
https://haveibeenpwned.com/.well-known/security.txt and you will see the result as a plain text like:
Contact: mailto:security@troyhunt.com